Cisco site-to-site VPN with outside VRF
TL;DR: Outside interface is a VRF, inside on global, must Specify VRF on crypto keychain.
I recently set up a IPSec VPN between two Cisco routers where the Internet-facing interface was in a VRF and the tunnel interface was in not in a VRF.
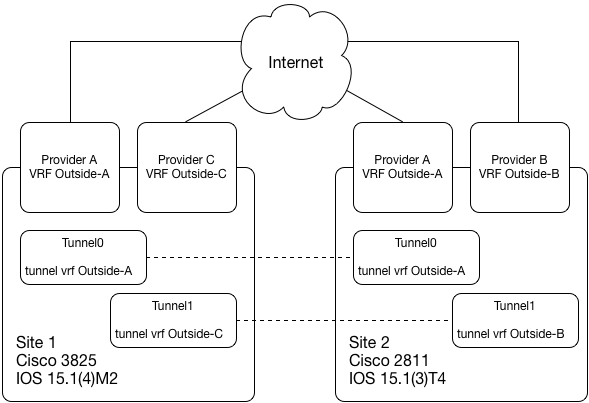
The VTI was configured in the usual way:
interface Tunnel0
description VPN: site2 via provider A
ip address 192.168.1.1 255.255.255.254
ip mtu 1438
keepalive 5 3
tunnel source 192.0.2.1
tunnel mode ipsec ipv4
tunnel destination 192.0.2.2
tunnel vrf Outside-A
tunnel protection ipsec profile vpn-to-site2-via-provider-a
!
With the usual crypto configuration:
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
lifetime 3600
crypto isakmp key SecretKey address 192.0.2.2
crypto ipsec transform-set vpn-peer esp-aes esp-sha-hmac
crypto ipsec profile vpn-to-site2-via-provider-a
set transform-set vpn-peer
but the tunnel wouldn’t come up.
“debug crypto isakmp” showed a error to the effect that a preshared key wasn’t configured or couldn’t be found for the peer. This was puzzling because there was clearly a preshared key defined.
There weren’t any messages in the debug logs about incoming connections or policy mismatches so I assumed that the problem was occurring before the router tried to communicate with its peer or it wasn’t seeing traffic from the peer.
From the documentation I found it seemed like the “tunnel vrf Outside-A” statement in the VTI was all that was necessary for IOS to know that the outside was in a VRF (the tunnel endpoint is in a VRF so the protection profile must be on the VRF as well). This turned out to not be the case. The vrf statement on the VTI is just for the tunnel. You need to specify the VRF in the crypto keyring definition otherwise the router isn’t looking for VPN traffic in the VRF.
I changed the crypto configuration to use a keyring and specified the outside vrf on the keyring definition:
crypto keyring vpn-peer vrf Outside-A
pre-shared-key address 192.0.2.2 key SecretKey
!
crypto isakmp policy 1
encr aes
authentication pre-share
group 2
lifetime 3600
crypto isakmp profile vpn-to-site2-via-provider-a
keyring vpn-peer
match identity address 192.0.2.2 255.255.255.255
keepalive 10 retry 5
!
!
crypto ipsec transform-set vpn-peer esp-aes esp-sha-hmac
!
crypto ipsec profile vpn-to-site2-via-provider-a
set transform-set vpn-peer
and now it all works. Of course now that it’s working I find a Cisco doc on New Version Site-to-Site Configuration that shows this.